Tech-Powered Hosting: How Digital Tools Transform Hotel Management

Hotel guests today do more from their phones than ever before — they book a room, check in remotely, order ...
Read more
How Applicant Tracking Software Revolutionizes Modern Hiring

Key Takeaways Applicant Tracking Software (ATS) automates and streamlines the recruitment process, enhancing efficiency. Modern ATS platforms offer advanced features ...
Read more
What Are the Most Common Cyber Threats Today?

Cyber threats have become more complex, widespread, and persistent in recent years. As digital activity increases and organizations depend more ...
Read more
Why Identity Has Become the Soft Underbelly of Enterprise Security

Most security teams feel well equipped. They run endpoint tools, cloud controls, and strong network filters. Yet breaches still spread ...
Read more
How to Choose the Right SEO Agency for Your Business
Key Takeaways Understand and prioritize your business’s SEO objectives before evaluating agencies. Choose agencies with industry-specific experience, proven methodologies, and ...
Read more
What “MyGreenBucks Net Jones” Really Is — Honest Guide
In recent years, many people searching for extra income opportunities or financial guidance online have encountered the phrase “MyGreenBucks Net ...
Read more
How to Fix the 418dsg7 Error: Causes, Solutions, and Prevention

The 418dsg7 error is a confusing and often frustrating issue that users encounter when software, applications, or digital systems fail ...
Read more
TGarchirvetech Gaming Trends: The Future of Gaming in 2025 and Beyond

The gaming world is in the middle of one of its most exciting revolutions ever, driven by profound technological shifts ...
Read more
Understanding Key Cybersecurity Terms and the IAM Framework
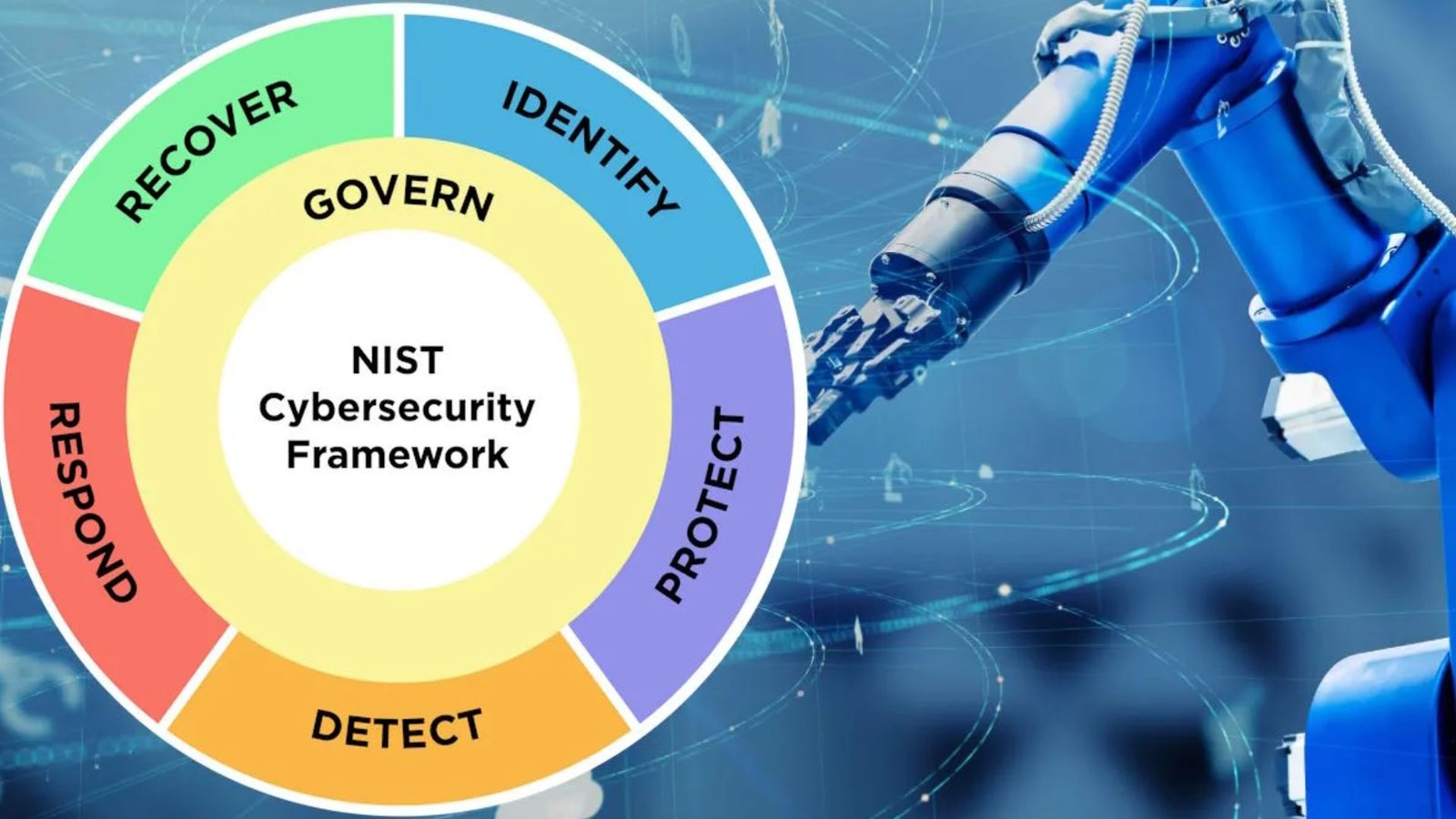
Cybersecurity shapes how organizations protect their data, systems, and users. Yet, many people misunderstand the core terms that drive security ...
Read more
Payroll Software Setup: Best Practices for Small Teams

Setting up a payroll system can be one of the most critical steps for any organization, especially for small teams ...
Read more